Operational Quantum Computing Built for Real-World Deployment.
We turn quantum technology into deployable capability—validated in the cloud, engineered on Novera hardware, and integrated for real-world operations.
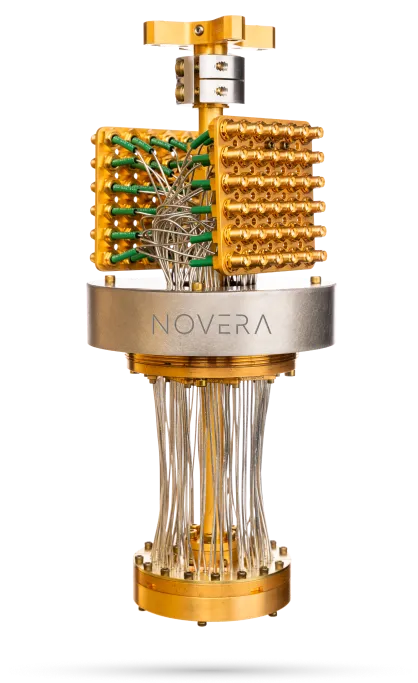

Light Rider transforms quantum computing from an emerging technology into a practical, mission-ready capability tailored to each customer’s most complex challenges. We collaborate with leading QPU, control, and cryogenic partners to deliver efficient, cost effective systems, first validating results on cloud based quantum platforms before deploying hardware. We then design and support customized solutions, along with the training and long-term strategies needed for sustainable adoption.








.avif)








.avif)
.avif)








.avif)








Q-Day refers to the moment when quantum computers become powerful enough to break the classical encryption systems that secure modern digital infrastructure. Because today’s public-key cryptography relies on mathematical problems that classical computers cannot realistically solve, a sufficiently advanced quantum computer would be able to decrypt protected data, intercept secure communications, and compromise national networks.
+ Read more
This risk extends to AI, intelligence systems, military communications, critical infrastructure, and any sensitive information currently encrypted but being collected by adversaries for future decryption.
Cryptocurrencies would face an equally significant impact. Most major blockchains, including Bitcoin and Ethereum, rely on public-key signatures that could be forged by a quantum-capable attacker, enabling theft of funds or manipulation of transaction histories. While post-quantum upgrades are being developed, transitioning global blockchain ecosystems will be complex and slow. Q-Day therefore represents a major turning point that will force governments, enterprises, and digital asset networks to adopt quantum-resistant security to maintain trust and stability.
Engineering the Networks of Tomorrow, Today
"Harvest now, decrypt later" (HNDL), is a cybersecurity threat where adversaries collect encrypted data today to decrypt it in the future, once powerful enough quantum computers are developed. This is a current risk because the data, once captured, is vulnerable to future decryption, even if current encryption is strong. The strategy relies on the assumption that classical encryption methods will be breakable by post-quantum computers.
Networks immune to anticipation and prediction operate on quantum principles that make their core signals fundamentally unknowable in advance. Every key, state, and transmission is generated in real time through quantum processes that cannot be forecasted, modeled, or reconstructed by any external observer. Even an adversary with perfect predictive capability would find no future state to anticipate, because the information does not exist until the moment it is created and measured. This architecture ensures communication pathways that remain secure against present, future, and even hypothetical predictive threats.
Safeguards that remain secure across all timelines, rely on quantum mechanics to ensure that information is never fixed, predictable, or revealable before its intended moment. Quantum states cannot be cloned, rewound, or pre-observed, which means that even an adversary with the ability to look ahead would encounter only randomness and collapse the data by attempting to measure it. These defenses maintain their integrity regardless of when or how a threat emerges, creating a communication environment that is resilient not just to today’s attacks, but to any scenario that could unfold in the future.
Data protected from threats that do not exist yet, is secured by quantum processes that generate information in real time, leaving nothing static for an adversary to analyze or anticipate. Because quantum states cannot be copied or measured without detection, any future attack method would fail before it begins. This creates a security posture that adapts instantly and naturally to unknown risks, ensuring that information remains safe even as new technologies and threat vectors emerge.
